Back in 2022 I first started working with Azure Virtual WAN, and wrote a blog post around deployment of the service using Terraform (https://jakewalsh.co.uk/deploying-azure-virtual-wan-using-terraform/). Since then I’ve worked with Virtual WAN on numerous deployments, bringing Cloud networking and Infrastructure as Code together to provide flexible and rapidly deployed networking environments – that take advantage of Microsoft’s Global Network.
If you are interested in seeing more about Microsoft’s Global Network infrastructure – check out the Globe view available here: https://datacenters.microsoft.com/globe/explore/
Throughout June 2025 I’ve also had a focus on Virtual WAN, with two Community speaking sessions covering the service in more detail. Both sessions focused on providing an introductory overview, covering aspects like:
-
What Virtual WAN is
-
How it can be used
-
Core Components
-
Security and Firewalling
-
Demo Environments
-
Resources to help get started
You can download slides from those sessions below:
As part of this post, I wanted to provide an update on some of the developments in Virtual WAN, links to additional resources, and more!
Routing Intent
One of the key changes since my last article on this (Back in 2022 – time flies!), is the availability of Routing Intent via Terraform. When I first wrote about Virtual WAN and Terraform, this was unavailable via the AzureRM provider (It was added in 2023 as Routing Intent became Generally Available – https://github.com/hashicorp/terraform-provider-azurerm/pull/23138).
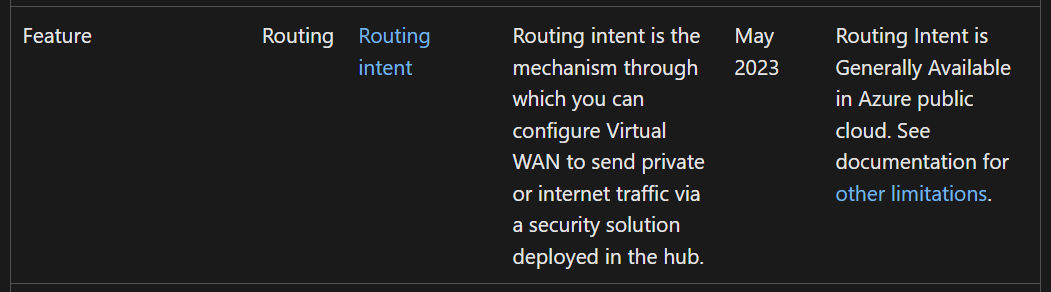
Here’s what needs controlling – we want all traffic routed via the Azure Firewall in my example:
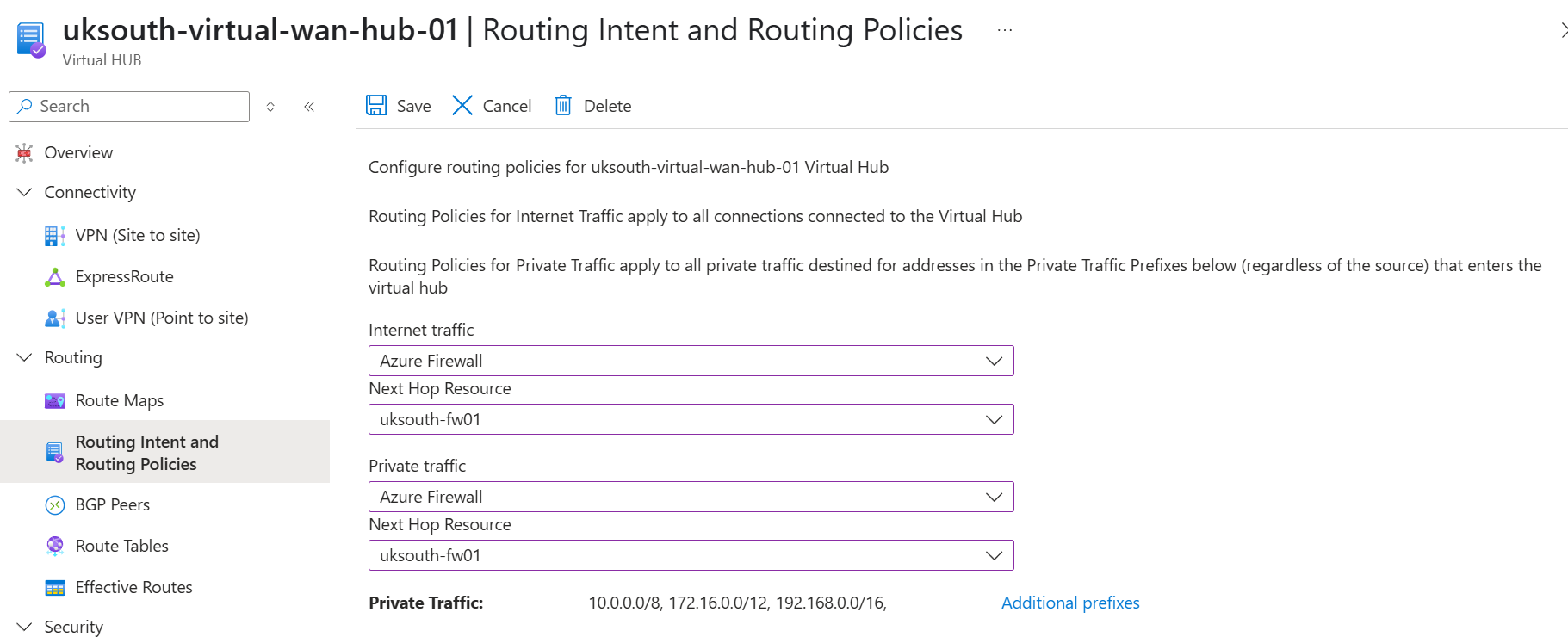
As you can see in the above – in the Portal we have the option of controlling how Routing Intent and Routing policies is configured. And within Terraform we can do this using the below block:
resource "azurerm_virtual_hub_routing_intent" "example" {
name = "example-routingintent"
virtual_hub_id = azurerm_virtual_hub.example.id
routing_policy {
name = "InternetTrafficPolicy"
destinations = ["Internet"]
next_hop = azurerm_firewall.example.id
}
}
You can read more about this here – https://registry.terraform.io/providers/hashicorp/Azurerm/latest/docs/resources/virtual_hub_routing_intent
Route Maps
Route Maps are a fairly recent feature for Virtual WAN, having been made Generally Available in April 2025. Route Maps provide a way to control route advertisements and routing for Virtual WAN hubs – giving more granular control over the routing within your Virtual WAN topology.
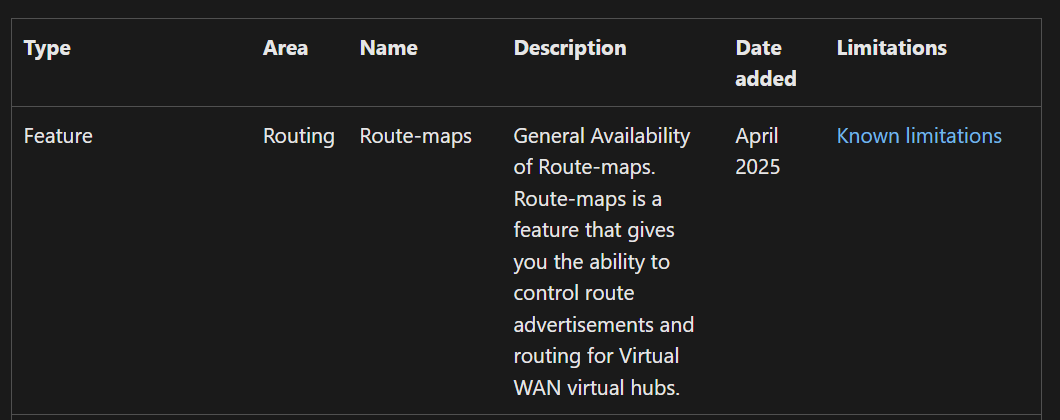
Route Maps enhance the capability of Virtual WAN further, providing additional control and flexibility – you can read more about Route Maps here: https://learn.microsoft.com/en-us/azure/virtual-wan/route-maps-about#why-use-route-maps
Note that Route Maps can also be configured using Terraform – see the example below, from the Terraform Registry:
resource "azurerm_route_map" "example" {
name = "example-rm"
virtual_hub_id = azurerm_virtual_hub.example.id
rule {
name = "rule1"
next_step_if_matched = "Continue"
action {
type = "Add"
parameter {
as_path = ["22334"]
}
}
match_criterion {
match_condition = "Contains"
route_prefix = ["10.0.0.0/8"]
}
}
}
https://registry.terraform.io/providers/hashicorp/azurerm/latest/docs/resources/route_map
Terraform Demo Lab:
As well as having ample resources to help – having access to a demo environment is also a huge help for Virtual WAN. Fortunately, I have an environment to help! My demo lab provides a fully functional environment that allows testing and development of Virtual WAN – including options around Azure Firewall too.
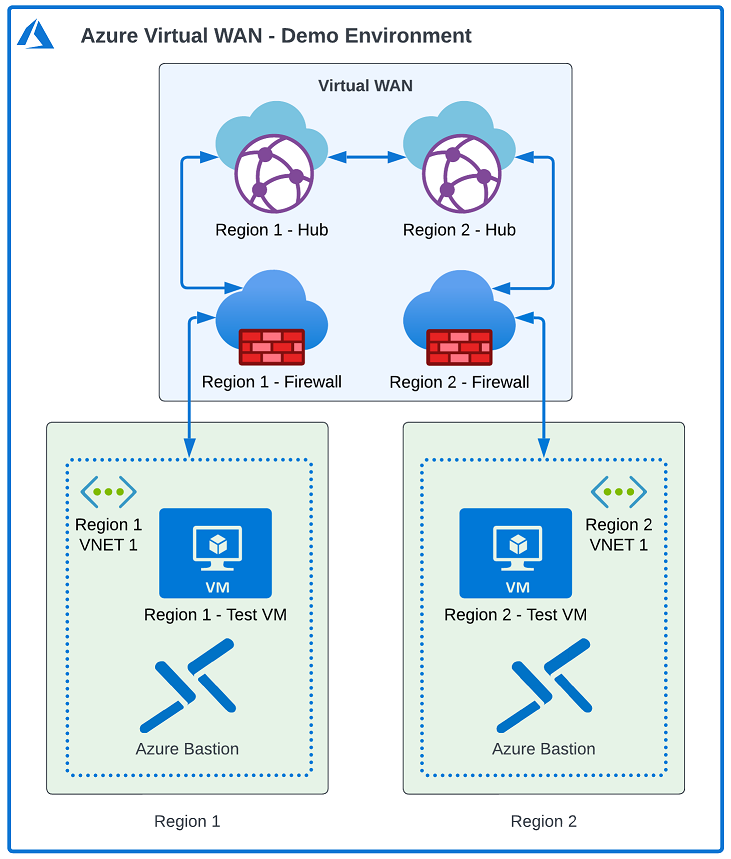
What does this Lab Deploy?
This lab deploys the following Resources:
- A Resource Group in two Azure Regions (based on variables)
- A Virtual WAN in the Primary Region
- A Virtual WAN Hub in two Azure Regions
- A vNet in each Azure Region which is connected to the Virtual WAN Hub.
- A Subnet and NSG in each of the above vNets.
- A Subnet in each Region to be used for Azure Bastion.
- Azure Bastion in each Region to allow for access to the VMs for Testing. (This is aimed at providing direct access to the VMs to allow quick testing in a lab / demo scenario).
- A Virtual Machine in each Azure Region (in the Regional vNets), to allow testing of Connectivity.
- A Custom Script Extension that runs on both VMs to add a few testing Apps (using Chocolatey) and disables Windows Firewall (as this is a demo / test environment).
Enabling Azure Firewall
To enable Azure Firewall set the following variable to true within the terraform.tfvars file:
# Optional - Firewalls azfw = false
The lab is deployed via Terraform – and you can download a copy here. I regularly maintain this environment (when possible). Feedback is always welcome on my demo lab environments – please use my contact form.
Wider Reading:
- Virtual WAN Route Map Overview (Microsoft Learn) – https://learn.microsoft.com/en-us/azure/virtual-wan/route-maps-about
- Virtual WAN – What’s New? (Microsoft Learn) – https://learn.microsoft.com/en-us/azure/virtual-wan/whats-new
- Glasgow Azure User Group – https://www.gaug.co.uk/
- Azure Bootcamp Switzerland – https://www.azurebootcamp.ch/
Until next time – thank you!